Special Report: The nature of cyber threat
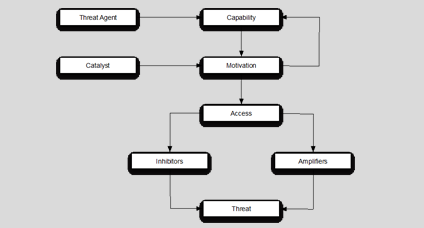
Fig.1
The past ten years have seen a rapid growth in sophisticated cyber attacks targeting intellectual property and capability. Cyber attacks such as Ghostnet, Stuxnet, Flame, Zeus and Duqu have all targeted intellectual property or capability associated within an organisation or individual. The recent arrests of the people behind the Silk Road hacking site clearly indicates that the criminal supply chain supporting malicious activities on the internet is sophisticated and mature. In order for us to protect our systems against sophisticated threat actors (STAs), we need to develop a detailed understanding of the nature of threats and the lifecycle of a cyber attack.
The intentional threat agent is a party that knowingly sets out to cause damage or loss to a system. The following are examples of the intentional threat:
| Threat type | Threat description |
| Foreign agents | These are people who professionally gather information and commit sabotage for governments. |
| Industrial or economic espionage | Corporate or industrial espionage involves operations conducted by one corporation against another for the purpose of acquiring a competitive advantage in domestic or global markets. |
| Terrorists | Terrorists use attacks to inflict fear and to achieve either social or political change. |
| Organised crime |
This threat arose because organised crime has realised that information has a distinct financial value attached to it and that information technology can be used to hide criminal activities. |
| Insiders | The biggest threat that any organisation faces is from its own employees. There are many documented cases where employees have sabotaged, modified or stolen information belonging to their employing organisation. |
| Hackers and crackers | This class of threat is often referred to as cyber-vandals. The image is generally that of a teenager breaking into a system for the fun of it and the recognition of his peers. |
| Political dissidents | These are people who are attempting to use information and information technology to achieve a political objective. |
| Vendors and suppliers | Vendors and suppliers are now integrated into the fabric of most organisations; for example, when we outsource IT functions to a third party, the security of the outsourcing organisations becomes critically dependent upon the security of the third party. |
Table 1 – Threat types and description
The problem that we face when dealing with threats and threat agents is the question of measurement. The potential of a threat agent to pose an actual threat to an information infrastructure will be influenced by a number of factors. In reality, for the threat agent to pose a real threat to an information infrastructure, the agent must possess a capability and must also be able to gain either physical or electronic access. Its level of capability will influence the impact that such a threat agent will have. The threat agent will be weakened by factors that will inhibit its ability to form a threat and will be strengthened by other factors. In addition, there will be some type of catalyst that will cause the threat agent to act, depending on his or her motivation. The components of ‘threat’ that apply to a malicious threat and their interrelationships are detailed in Fig. 1.
Threat agent
The threat agent element expands into the types of threats that may be seen. These have, for convenience and because they can be dealt with in a number of very different ways, been subdivided into two different groups: the natural threat agents and the malicious threat agents. These are a relatively well-understood set of threats, and there is actuarial history of the effects of fire, wind, water and earthquake components that is based on long-established experience within the insurance industry. A malicious threat can be divided into the categories defined in Table 1.
Capability
In order for a malicious threat agent to be effective, he or she must have the capability to conduct and sustain an attack or to totally destroy the system and any replacement. The components of a capability can be divided into the following categories: a) software, b) technology, c) facilities, d) education and training, e) methods and f) books and manuals. For malicious threat agents to carry out an attack, they must have the means and the necessary skills and methods to be successful. We can also measure capability as a maturity function.
| Capability level | Threat capability description |
| 1 (Very low) | This type of capability is associated with little technical knowledge and the use of open source tools and scripts. |
| 2 (Low) | This type of capability is associated with limited technical knowledge and the use of open source tools and commercial tools. |
| 3 (Medium) | This type of capability is associated with good technical knowledge and the use of open source tools and commercial tools in a repeatable manner. |
| 4 (High) | This type of capability is associated with sophisticated threat actors backed with a good knowledge development capability and reasonable resources. |
| 5 (Very high) | This type of capability is associated with national state actors with unlimited funds and backed by a sophisticated research and development infrastructure. This type of threat capability is typically attributed to a foreign intelligence service. |
Threat inhibitors
A threat inhibitor is any factor that decreases either the likelihood of an attack taking place or the likelihood of an attack being successful. Of the factors that were identified, those that are detailed below were considered to be the most significant. Taking each of these factors in turn:
- Fear of capture: If the threat agent has the perception that, if they initiate an attack, they are likely to be identified and captured, this will act as a deterrent and will inhibit the perpetrator;
- Fear of failure: If the threat agent believes that they are likely to fail in their attempt to conduct an attack, this may act to deter them from trying. This effect will be further enhanced if they are sensitive to the opinions of others and believe that they will know the failure;
- Level of technical difficulty: If the defences of a target that has been identified by a threat agent are shown to be difficult to overcome, then this will, in most cases, reduce the likelihood of the threat agent attacking the system as the threat agent will search for a less challenging target. In some cases this may be inverted as the threat agent will attack the most difficult of targets to prove or demonstrate their skills and abilities;
- Cost of participation: If the cost of undertaking the attack is too high, then this will inhibit the threat agent from initiating the attack. The cost may be in terms of finances, appropriate equipment, time or information;
- Sensitivity to public perception: If the target that the threat agent has selected is one that would gain the threat agent disfavour in the eyes of the public, this may act as a deterrent. The sensitivity of the threat agent to the public’s feelings may inhibit the action;
- Law enforcement activity: If the laws within the target country or the country from which the threat agent is operating are strong, relevant laws that have been tested in the courts have been shown to be effective and the law enforcement community is seen to be aggressive in its application of the law, this will act as an inhibiting factor;
- Target vulnerability: If the target that the threat agent has identified is perceived to be in a well-protected state or if the system is thought to be protected by a variety of devices, this should inhibit the likelihood of the threat agent undertaking the attack;
- Target profile: If the profile of the target is such that, in comparison to similar organisations, it is less attractive to the threat agent, this will inhibit the likelihood of an attack;
- Public perception: If the perception of the public is in favour of the organisation that the target represents, then this will reduce the likelihood of a threat agent carrying out an attack; and
- Peer perception: If the consensus of opinion of the threat agent’s peers is that the target would be ‘poor’ for reasons of ease of access, resulting in no peer acknowledgement for a successful attack, or because the business of the target receives the support of the peers, then this decreases the likelihood of an attack.
Threat amplifiers
A threat amplifier is any factor that increases either the likelihood of an attack taking place or the likelihood of the attack being successful. Of the factors that were identified, those that are detailed below were considered to be the most significant. Taking each of these factors in turn:
- Peer pressure: A threat agent is more likely to carry out an attack if they feel that to do so will advance their prestige or status within their peer group. Particularly within hacking circles, elevated status and regard by other hackers will gain the individual access to information and resources that they did not have before and will also achieve one of their aspirations of increased status within the community;
- Fame: In all social groupings, a proportion of the individuals will seek to be recognised for the actions that they have undertaken;
- Access to information: If an individual or group believes that they will gain access to information that is of use to them, either as a direct result of carrying out an attack or as an indirect reward for it, they will, in some cases, be more inclined to carry out the attack;
- Changing high technology: As technology has advanced, a recurrent theme has developed: release of a new technology, acceptance into common use, discovery of weaknesses in the technology, then exploitation of the weaknesses for illicit purposes;
- De-skilling through scripting: As new techniques to subvert the security of systems are understood, the more skilled attackers, most particularly from the hacking community, will write scripts that will automate the attack;
- Skill and education levels: As the general level of education with regard to technology increases and the use of technology becomes almost ubiquitous, and as the skill level with regard to the use of new technologies increases, so the number of people who understand both technology and ways to carry out attacks will rise;
- Law enforcement activity: The following characteristics with regard to law enforcement may influence a threat agent to attempt to carry out an attack:
- If the laws within the target country or the country from which the threat agent is operating are perceived to be weak or not relevant to the types of activity that the attackers are using;
- If the laws that are being used have not been tested in the courts or have been tested and shown to be ineffective; and
- If the law enforcement community is seen to be reluctant in its application of the law, this will act as an amplifying factor.
- Target vulnerability: If the target that the threat agent has identified is perceived to be in a poorly protected state, or if it has vulnerabilities that come into effect through no fault of the system management, this may amplify the likelihood of the threat agent undertaking the attack;
- Target profile: If the profile of the target is such that, in comparison to similar organisations, it is more attractive to the threat agent, this will amplify the likelihood of an attack; and
- Public perception: If the perception of the public is against the organisation that the target represents, then this will increase the likelihood of a threat agent carrying out an attack.
Threat catalysts
Threat catalysts are those factors or actions that cause an attack to be initiated at the time and on the target that is selected. Again, the catalyst may be either real or perceived. The main groupings of threat catalysts have been identified as:
- Events: An event may be related to the attacker or to the target, either directly or indirectly. An event that influences the threat agent might be a personal experience or exposure to news that triggers predetermined actions;
- Technology changes: A change in technology occurs at approximately nine-month intervals, and as a result, new uses for technology become apparent, and also shortcomings in the technologies that are in use become understood in the wider community; and
- Personal circumstances: A change in the personal circumstances of the threat agent may result from exposure to information that affects their values or beliefs.
Threat agent motivators
The factors and influences that motivate a threat agent are diverse and may operate singly or in unison. The primary groupings of threat agent motivators are detailed below, together with a general description. The main motivational factors are:
- Political: The threat agent may be motivated by a wish to further the cause of a political organisation or further his or her own position within the political grouping;
- Secular: If the motivation of the threat agent is to support their secular beliefs, it is possible that the level of action that they will be prepared to take is quite high. A person that is supporting their secular beliefs will be likely to pursue an attack to a final conclusion;
- Personal gain: There are a number of aspects that have been grouped together under this general descriptor, as individuals are motivated by different rewards and gains;
- Religion: Religious conflicts are amongst the most common, and as a result it is to be expected that this will be a major motivational factor for a threat agent;
- Power: If an individual seeks to gain or to demonstrate that they have gained power, they may choose to demonstrate their capability through an attack on an information system;
- Terrorism: The use of information systems by terrorists for the purpose of information dissemination and propaganda; and
- Curiosity: This motive is strong and difficult to quantify. As it is normally unfocused and will only be directed at the target in question while the curiosity lasts, it is difficult to predict or to determine when the threat agent will have sated their curiosity.
Summary and conclusions
In this paper I have outlined the various elements associated with the nature of threat. In particular, I have presented a structured framework within which research and development activities can be placed and structured so as to have the best impact against an adversary. The goal of this framework is to allow people to develop and deploy capability that best mitigates threats.
Professor Andrew Blyth
School of Computing
University of South Wales
tel: +44 (0)845 576 7778
http://www.southwales.ac.uk